- Home
- >
- Offshore News
- >
- Identify and Address Data Security Risks for Remote Workers
Amidst the heat of the pandemic, remote work has become the norm in the modern workplace. In April 2020, Zoom – the popular video conferencing tool, experienced a significant data breach that compromised the accounts of approximately 500,000 users. Hackers exploited weak security controls, leading to unauthorized access to virtual meetings and personal information. The exposed data included email addresses, passwords, and personal meeting URLs, which were sold on hacker forums.
The Zoom breach underscores the importance of robust cybersecurity practices for remote teams. With technology enabling companies and employees to work from anywhere, safeguarding data from security breaches becomes more crucial than ever.
This blog discusses how to keep your data secure when working with a remote team. It covers common security risks and provides practical solutions to protect your sensitive information.
Key Summary
The article from InApps.net, referencing the 2020 Zoom data breach affecting 500,000 users, highlights the critical need for robust cybersecurity in remote work environments. It outlines common risks and practical solutions for securing data. Key points include:
- Common Data Security Risks:
- Hacking/Social Engineering: Attackers target developers with disguised emails to steal project credentials, compromising source code and data.
- Phishing: Fake websites mimicking tools like GitHub or Slack trick users into revealing login details.
- Malware/Ransomware: Malicious software, including spyware and ransomware, can lock systems or steal data, exploiting remote workers’ online activities.
- Data Protection Tips:
- Create Strong Passwords: Use complex, unique passwords (e.g., P@ssw0rd!23$X) with at least 12 characters and enable multi-factor authentication (MFA).
- Secure Devices: Use work-only devices with updated software, antivirus, and custom malware protection; implement Mobile Device Management (MDM) and Mobile Application Management (MAM).
- Use Cloud Services: Opt for secure platforms like Google Drive or Dropbox with strong passwords for safe collaboration.
- Avoid Public Wi-Fi: Use VPNs (e.g., NordVPN, ExpressVPN) or mobile hotspots for encrypted connections; avoid sensitive tasks on public networks.
- Build a Data Security Policy:
- Data Protection: Enforce encryption for data in transit/rest and restrict access to authorized users.
- User Authentication: Mandate strong passwords and MFA.
- Training & Communication: Conduct regular security training, update policies promptly, and provide clear breach response protocols.
- Conclusion:
- Remote work increases vulnerability to data breaches, requiring robust measures, employee education, and proactive vigilance to ensure a secure environment.
1. Common Data Security Risks for Remote Workers
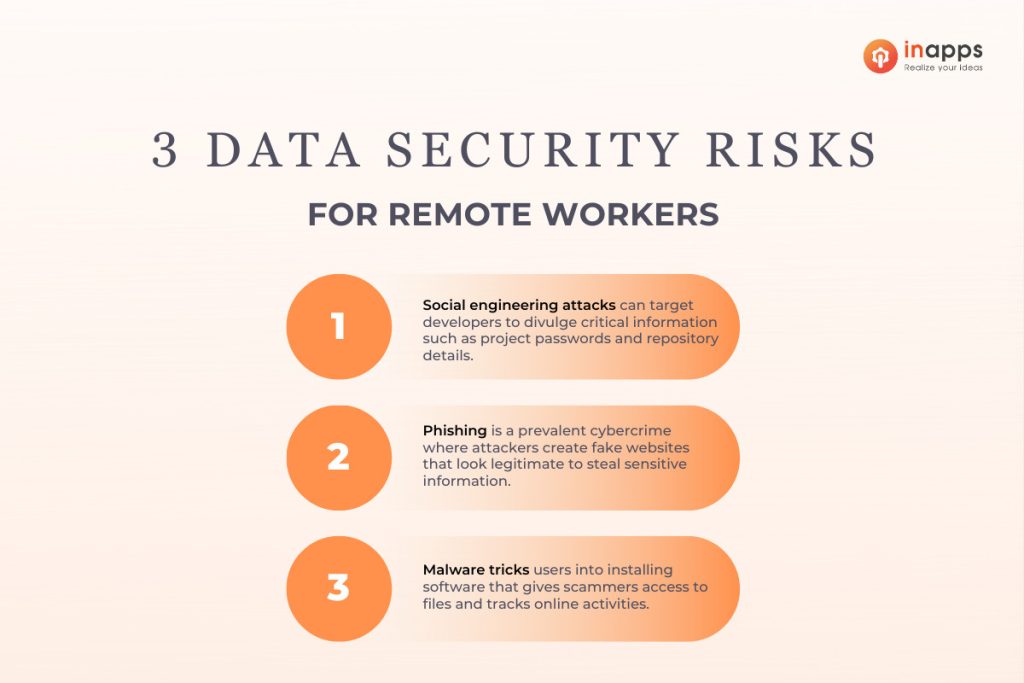
1.1 Hacking Or Social Engineering:
1.2 Phishing
Phishing is a prevalent cybercrime where attackers create fake websites that look legitimate to steal sensitive information. For remote development teams, these attacks might involve fake websites resembling popular tools like GitHub or Slack, tricking developers into entering their login credentials. These websites often present urgent problems requiring verification of personal information, posing as company tools, or pretending to be a manager or colleague.
How it looks:
- A website that mimics a legitimate development tool but has a different URL.
- It presents an issue requiring immediate action, such as verifying your information through a provided link.
- It may ask for donations to a fake charitable cause or notify you that you’re a winner.
- It can ask for urgent help while pretending to be a colleague or supervisor.
Remote developers often become easy targets for these attackers, as they regularly use various online tools and services, making it easier for phishing attempts to go unnoticed.
1.3 Malware and Ransomware
2. Data Protection Tips For Remote Workers
2.1 Create A Strong Password
Instruct your team to use unique, complex passwords for different platforms and change them regularly. Implement multi-factor authentication for an added layer of security. Use passwords with a mix of letters, numbers, and special characters, and ensure they are at least 8 characters long.
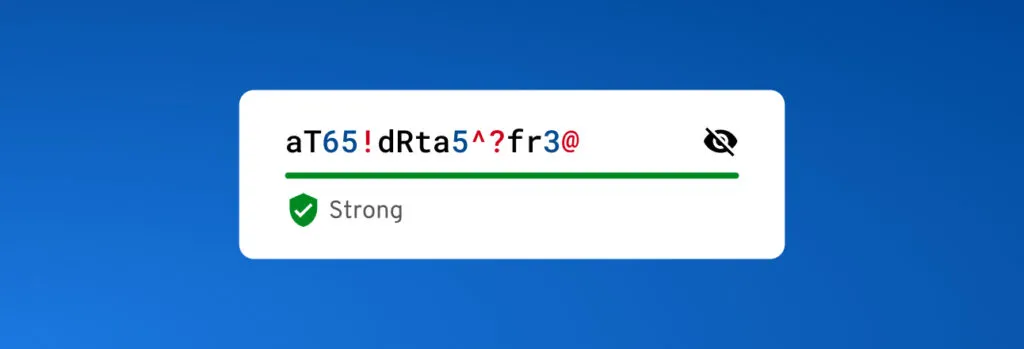
Example of a strong password
Let’s say your remote team member needs a password for their project management tool. Instead of using a simple password like “project123”, they should create a more complex one such as “P@ssw0rd!23$X”.
2.2 Secure Devices
2.3 Use Cloud Service
Cloud services facilitate real-time collaboration and secure file sharing. Choose reputable providers like Google Drive, OneDrive, or Dropbox. These platforms not only offer seamless collaboration but also ensure your data is stored safely. Make sure to use strong, unique passwords to protect your cloud data.
Cloud services provide a secure virtual storage and working environment, significantly reducing the risk of data breaches. This way, you can focus on your work, knowing your data is safe and accessible.
2.4 Avoid Public WiFi Or Use Secure Connection (VPN) Instead
Public internet networks are not secure and can be easily accessed by hackers. Remote employees should avoid using public Wi-Fi for sensitive communications. When not in use, turn off Wi-Fi and Bluetooth connectivity on devices.
In cases where remote workers have to use public wifis, follow these practical steps. Always use a VPN (Virtual Private Network). A VPN encrypts your internet connection, making it difficult for hackers to intercept your data. Services like NordVPN, ExpressVPN, or CyberGhost are reliable options. Alternatively, use your phone’s mobile hotspot if possible. This is generally more secure because it limits the number of users who can access your network.
Use VPN for better data security for remote teams
3. Build a data security policy for remote workers
Creating a comprehensive security policy is essential for protecting company data. Ensure remote employees understand and follow these policies. In the policies, you should mention:
Data Protection
- Encryption: Use encryption for data in transit and at rest.
- Access Control: Restrict data access to authorized personnel only.
User Authentication
- Strong Passwords: Require complex passwords and regular updates.
- Multi-Factor Authentication (MFA): Implement MFA for additional security.
Besides, it’s important to hold these training sessions frequently so that everyone remains aware of the latest risks and the best practices for avoiding them. Additionally, any updates to the security policy should be communicated immediately to ensure that all employees are informed.
Also, employees should know exactly who to contact and what steps to take if they encounter a security breach. This way, issues can be addressed quickly and efficiently.
4. In conclusion
Let’s create the next big thing together!
Coming together is a beginning. Keeping together is progress. Working together is success.