- Home
- >
- Blockchain & NFT
- >
- WHAT YOU MUST CONSIDER BEFORE IMPLEMENTING BLOCKCHAIN TECHNOLOGY
With the world of cybersecurity constantly evolving, it’s essential to stay ahead by adopting new technologies. Blockchain technology has come forward as one way you can protect your codes from being compromised and make sure they’re never lost again!
Product owners entrust their development team with the credibility of ownership of the written code and the certainty that the product will function properly throughout the software development process. This is a big deal because the authenticity of digital products is being pushed hard across all industries, with enormous ramifications for companies that have products based on potentially stolen codes.
This article will discuss the importance of securing software codes and how Blockchain technology can help with this.
Read more: Why is the world go crazy with Blockchain – real examples?

Why do you need to secure code?
When was the last time you heard someone say: “I can’t believe they didn’t secure code.”?
Code is the language that enables communication between all of your website’s systems, including visitors to it. Without secure code, just about everything on your site can be used by hackers in some fashion- whether they want information like passwords or their email address for spamming later!
And while you might think these things don’t matter because no one will ever know what was seen when reading our content. Guess again. The more people targeted with malicious links online, the greater the risk someone may try something against them eventually, at least once, if not multiple times over time, until finally succeeding.

Everyone active on the internet needs to be aware of how important to protect one’s code. As more and more people store sensitive information online, they are putting themselves at risk for hacking or identity theft if their computer credentials fall into the wrong hands!
Hence, “Why do you need to secure code?”. It’s crucial for several reasons:
- Your business and personal data are at risk when it comes into contact with the public internet. They may not be as concerned about hacking, but we know that any reputable company will always take their cybersecurity seriously. This means ensuring employees don’t have access credentials like usernames/passwords, etc., along with protecting against SQL injection attacks by sanitizing input – even if they’re internally generated such as form fields or HTML markup language.
- When your code is not secure, your product’s end-users (consumers) may receive security warnings that discourage software downloads.
- The launched digital product (software solution) may be withdrawn entirely due to unauthorized code use.
- Exposure to numerous legal violations and the complex process of resolving them.
- The negative impact of exposing a software vulnerability on both the product and the company.
- Codes are written daily for these product launches, and proving ownership of these written codes is becoming increasingly difficult.
Ownership of the Code
Startups, enterprises, product companies, and other small and large businesses with digital software products must demonstrate code ownership for the products they release to the digital market. Inability to do so has resulted in high-profile cases worth billions of dollars.
As a result, in-house or offshore software outsourcing firms are now putting in the extra effort, signing outsourcing contracts to assign ownership of code and using various technological processes to secure these codes used in bringing product solutions to life.
This means that the software development partner must write the code themselves, rather than copying it from other sources, demonstrating that they did so. If a software development company assigns code ownership to a client for code they did not write, this is code theft, resulting in a slew of legal complications.
The following factors are taken into account during the code ownership journey:
- The software programmers or remote developers you hire use processes to store all transaction records securely.
- Code signing differs from SSL in that developers sign the codes to prove ownership.
- The entire development process should be documented with dates and timestamps.
- The times have changed, and software companies are implementing various technological processes to prove code ownership, one of which is Blockchain technology.
Blockchain technology explained
The concept of Blockchain is still new and complicated in many ways. It’s often difficult for people with no technical knowledge to understand the ins and outs, let alone how this technology will affect their lives or businesses when they least expect it! But don’t fret – we’re here to break down some simplifications on what exactly Blockchain Technology does so you can get down.
Blockchain is a system that allows the storage and transmission of data without relying on trusted third parties.
By using Blockchain, an individual’s identity can be verified through multiple systems such as ID cards or smartphones alone instead of having only one form to submit with every transaction; this improves security because no single point of failure exists in these networks, which means there’ll never come back fake documentation after losing it during travel for example!
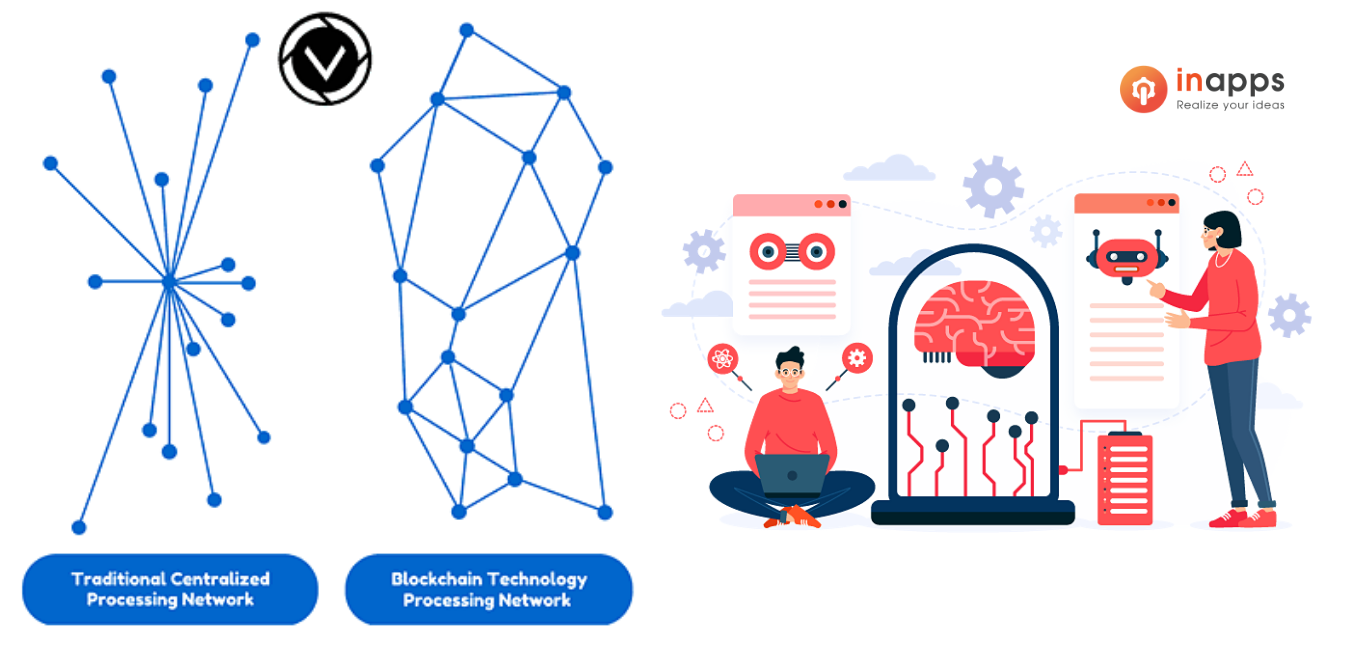
In blockchain technology, data structures are stored in blocks linked in a cryptographic chain to ensure security. Furthermore, the decentralized system process ensures that all transactions within the data block are validated solely through the participation of members via a consensus mechanism. The apparent complexity of the blockchain technology process is what makes it difficult to infiltrate and tamper with.
Blockchain technology is based on some fundamental principles that ensure network security.
- The use of a decentralized system eliminates the need for centralized servers. This means that there is no way to compromise all servers, disrupt the network’s mechanism, or alter existing data.
- In transaction processes, the use of a “peer-to-peer” (P2P) network.
- The use of modern data encryption technology enables digital signatures to sign transactions by all participants.
- Individual data blocks on the network are secured using the cryptographic chain format.
- The immutable records amass a trail of dates and timestamps, as well as the author’s information.
The application of blockchain technology in software security offers a comprehensive tamper-proof system that relies on cybersecurity frameworks and cryptographic protection.
Learn more: How to create a cryptocurrency – a guide for beginners
Using Blockchain Technology to Secure Codes
The outlined blockchain technology principles demonstrate that the system contains an immutable database. This means that the use of blockchain technology in code security is tamper-proof, and you can easily prove ownership of your company’s written codes while also identifying code theft perpetrators.
You can even hire blockchain developers to infuse blockchain power into your software while securing the codes with this technology.
The Blockchain uses cryptography for users who have access to numbers on their devices. Each block of information has its verification process before adding onto an existing chain which makes hacking virtually impossible.
Blockchain technology is a new and exciting way to process information. Before implementing this change, many things need consideration, such as:
- The ability for data storage on the Blockchain: Security risks associated with compromising or hacking into networked devices
- Which type of transactions will be enabled by utilizing its use? Who gets priority when it comes time for confirmation (transaction)?
Before implementing blockchain technology, you must consider the following:
- How do I know this will work?
- Is there room for error in my plans, or does it require 100% commitment?
- If something goes wrong, who am I going to turn too and what might they be able to offer me as support
- What are some potential problems that may arise during the implementation of Blockchain Technology?
View more: Will Blockchain lead the future technology?
Tips for securing codes with Blockchain technology
Segmentation: Choose what information you want to capture on each data block.
Management of one’s identity: This ensures encryption and blocks vital management processes. When it comes to securing your code on the Blockchain, you must decide whether to reveal the code’s content (using the zero-knowledge-proof technique).
Gaining network access: Choose the people who will have access to your data. As a result, you can designate your blockchain network as private or public, granting identity access and permission control as desired.
Recovery from a disaster: Create a disaster recovery template for participants.
Maximum protection: To ensure the security of your solutions and to protect against governance, business, and technology risks, build your security and risk model on top of the existing blockchain system.
System of control: To protect trust, privacy, and security, establish and define security controls across your blockchain network.
After successfully securing ownership of your codes as blockchain transactions, you can create smart contracts with conditions allowing only authorized parties to use your code.
How to choose the right Blockchain experts
Blockchain is hot, and it needs to be. So how do you know who’s got your back? How do you know if a blockchain expert is right for your business?
The right blockchain experts can make all the difference in your success. Find out who they are, what sets them apart from others, and how you’ll benefit by working with them!
Consult industry magazines, review platforms such as Clutch, or websites that list professional services to find out what they specialize in and who their clients are so there’s no confusion about which service will work for your needs!
The use of blockchain technology in software security is new, but it has proven to be highly beneficial in various processes. Although a highly complex procedure, it is still evolving into various segments to provide tamper-proof security across all industries.
As a result, you must seek out a software development firm with blockchain development solutions, such as InApps Technology, to build products and secure your code ownership for all digital content. We are ranked 1st of Top Blockchain development company in Vietnam on Clutch.
Maybe these articles are helpful for you:
NON-FUNGIBLE TOKENS QUARTERLY REPORT Q2 – 2021
NFT IN A NUTSHELL: EVERYTHING YOU NEED TO KNOW
Let’s create the next big thing together!
Coming together is a beginning. Keeping together is progress. Working together is success.












